
You may enjoy an occasional day of fishing on the lake, but the phishing we’re talking about today isn’t nearly as fun. Similar to regular fishing, phishing involves the use of bait to draw in unsuspecting users for nefarious purposes. Cyber criminals use various phishing techniques, usually through email, to convince users to reveal sensitive information that should never be shared.
In this article we will share examples of some common phishing techniques used that can infiltrate your business email system and makes its way to unsuspecting users who aren’t trained to keep an eye out for these types of attacks.
Especially as more employees are working from home, and sometimes required to use their personal computers, it’s important that they understand the value of recognizing a suspicious email and take the appropriate actions.
Generally speaking, there are three ways that hackers use to phish for data. One method is to include an attachment in an email that, once opened, scours your computer to collect information. Another tactic is to place a link in the email that will lead you to a dodgy website.
Many people are fooled by this method into thinking that they are viewing the website of a legitimate business, such as a financial institution. And thirdly, the email may request that you reply with confidential information. Every user should be educated and warned about these potential threats. Here are some real-life examples:
Financial Institutions do not Solicit Information through Email
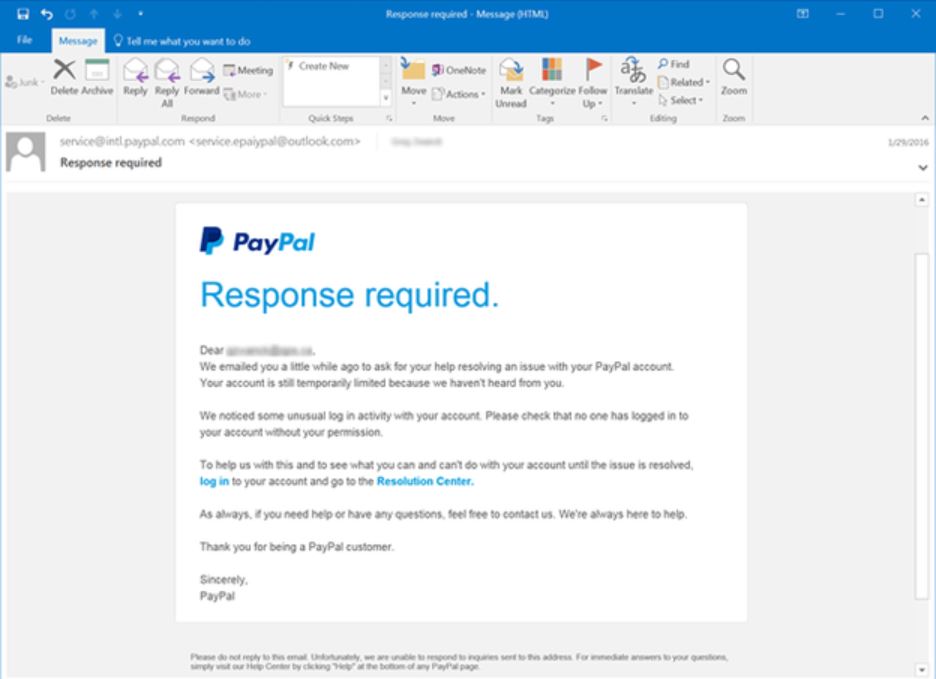
Example: PayPal
The website phishing.org offers a variety of resources for combatting the phishing hack. One of the examples they give is shown in the screenshot below. The sender of the email is hoping that the user will think it’s actually coming from the money transfer company Paypal. As the saying goes, looks can be deceiving. While it appears to be official, there are some clues that will help the wary user to avoid the phishing trap.
Knowing the proper URL of the company in question is important. Any emails from Paypal should come from the first-level domain paypal.com.
Take a closer look at the email address of the sender, and if the URL shows anything else, take that as a red flag.
You can also hover over the link in the email body without clicking on it. This will give you the URL destination that you’re asked to visit. If any of these seems questionable to you, don’t click. Better safe than sorry!
Users should also be aware that legitimate financial institutions generally do not solicit information through emails. If you were not expecting an email from the company, such as a response to your request for a password change, be very careful before taking any action.
Low Resolution Images and Refund Claims
Example: IRS Tax Refund
The security company Norton offers further insight into the illicit practice of phishing. One of the examples they provide concerns an email purporting to have identified a refund that you are due from the IRS. Norton offers the tip that sometimes these emails come through with a low-resolution logo.
Poor Grammar and Spelling in Emails is a Strong Key
Example: SunTrust
Another dead giveaway is when you see poor grammar or spelling in the email. In this example from Norton, any educated reader would notice the poor grammar in the first paragraph. These phishing attacks often originate from countries where English is not the first language. Sometimes it’s quite obvious at first glance that the email is fake, but be sure to read carefully before taking any action. And when in doubt, don’t!

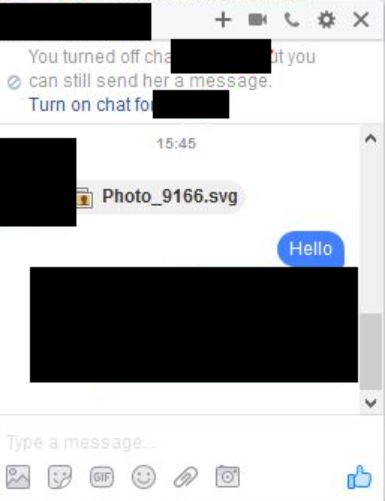
Avoid Unknown Attachments, even from Social Media Channels
Example: Facebook Messenger
The phishing exploit is not limited to email, however. Take a look at the screenshot below. It seems that clever hackers are busy on social media as well. Somehow they are even able to hack a friend’s account and send an attachment in the Facebook Messenger app. Users should be extremely careful about opening attachments on social media. Some Facebook users avoid Messenger for that very reason.
Phishing Scams to Look Out For
Cyber attackers may pretend to be a financial institution, as shown above. But users should be on guard against other possible ploys that phishing hackers may use. Another method is to present an offer of money to get the user to reply with contact or financial information. We’ve all heard of the old “Nigerian Prince” scam. Don’t fall for it. If it sounds too good to be true, it probably is.
Other Examples Common in the Workplace
You should also watch for emails from someone pretending to be your boss, or a colleague asking for your login. Always double check the sender’s email address if the email seems to come out of the blue. And if you really want to know the truth, you can give that person a call to verify that the email is really from them.
It's also common to get emails that sound as if an invoice is waiting for your approval, or is past due. Unless you are in billing and are expecting the email, report it to your IT Admin.
And yet another tactic used by hackers is to pose as charity organizations. The FCC warns citizens to be especially on the alert after disasters such as major storms. They gave these general tips on their website:
Donate to trusted, well-known charities.
Verify all phone numbers for charities.
Do not open suspicious emails.
Impact of Phishing on Businesses
Phishing can be devastating to your business. According to Check Point, the security software company, the average successful phishing scam can cost a company $7.9 million. They also cite a Verizon 2019 Data Breach Investigations Report that says phishing attacks make up 32% of all security breaches.
The truth is that careless actions of a single employee can make an entire confidential database open to an attacker. (In 2016, for instance, a presidential campaign manager clicked on a link and exposed all his emails -- quite an embarrassment!) It just takes one person to unwittingly share login information to a hacker, that can bring down the whole company.
Conclusion
IT admins have a lot of responsibility, but they should also advise the users they support of theirs. One weak link can break the chain. Each user should become aware of potential phishing scams and how to avoid them. Perhaps the best thing to remember is that you can never be too careful.
Hackers are looking for any opportunity to compromise your IT systems, and the internet is full of stories where individuals have caused organizations a lot of grief. Constant vigilance is the key, but taking the bait from a phishing attacker can lead to disaster. Be alert.
Contact us to learn more about how you can strengthen your security and see what other professional IT services we offer.
If you enjoyed this article you may also enjoy:
